Block cipher mode of operation: Difference between revisions
CSV import |
CSV import Tags: mobile edit mobile web edit |
||
| Line 25: | Line 25: | ||
[[Category:Block ciphers]] | [[Category:Block ciphers]] | ||
{{Cryptography-stub}} | {{Cryptography-stub}} | ||
== Block cipher mode of operation gallery == | |||
<gallery> | |||
File:BlockCipherModesofOperation.svg|Block Cipher Modes of Operation | |||
File:GCM-Galois Counter Mode with IV.svg|GCM Galois Counter Mode with IV | |||
File:ECB encryption.svg|ECB Encryption | |||
File:ECB decryption.svg|ECB Decryption | |||
File:Tux.svg|Tux | |||
File:Tux encrypted ecb.png|Tux Encrypted ECB | |||
File:Tux encrypted ctr.png|Tux Encrypted CTR | |||
File:CBC encryption.svg|CBC Encryption | |||
File:CBC decryption.svg|CBC Decryption | |||
File:CBC example v3.svg|CBC Example v3 | |||
</gallery> | |||
Latest revision as of 05:22, 3 March 2025
Block cipher mode of operation refers to the technique used to enhance the effect of a cryptographic block cipher. Block ciphers process blocks of fixed sizes, typically 64 or 128 bits, transforming them into encrypted blocks of the same size using a symmetric key. However, simply encrypting blocks of plaintext independently would not be secure against various attacks, such as pattern analysis. Therefore, modes of operation are employed to provide confidentiality or authenticity beyond the capabilities of a block cipher when used alone.
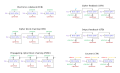
Electronic Codebook (ECB)[edit]
The simplest mode is the Electronic Codebook (ECB) mode, where each block of plaintext is encrypted independently. This mode has the disadvantage that identical plaintext blocks are encrypted into identical ciphertext blocks; thus, it does not hide data patterns well. Consequently, ECB is not recommended for use in cryptographic protocols that require data confidentiality.
Cipher Block Chaining (CBC)[edit]
Cipher Block Chaining (CBC) mode adds a feedback mechanism to the encryption process. Before a plaintext block is encrypted, it is XORed with the previous ciphertext block. This mode requires an initialization vector (IV) for the first block. CBC has been widely used due to its ability to hide repeated patterns in the plaintext.
Counter (CTR)[edit]
The Counter (CTR) mode converts a block cipher into a stream cipher. It generates the next ciphertext block by encrypting successive values of a "counter". The counter can be any function that produces a sequence that does not repeat for a long time, typically a simple incrementing counter. CTR mode has gained popularity because of its simplicity and performance advantages over other modes.
Galois/Counter Mode (GCM)[edit]
Galois/Counter Mode (GCM) combines the counter mode of operation with a Galois field multiplication operation to provide both data confidentiality and authenticity. GCM is widely used in applications that require both encryption and authentication, such as TLS and IPsec.
Output Feedback (OFB) and Cipher Feedback (CFB)[edit]
Both Output Feedback (OFB) and Cipher Feedback (CFB) modes turn a block cipher into a synchronous stream cipher. In OFB, the encryption is applied to a feedback value which is then XORed with the plaintext to produce the ciphertext. In CFB, the previous ciphertext block is encrypted and the output is XORed with the plaintext to produce the next ciphertext block. These modes are used in applications where error propagation needs to be minimized.
Authenticated Encryption with Associated Data (AEAD)[edit]
Modes like GCM and CCM (Counter with CBC-MAC) provide Authenticated Encryption with Associated Data (AEAD), which ensures the confidentiality, integrity, and authenticity of both the encrypted data and associated data (data that is not encrypted but whose integrity is protected).
Security Considerations[edit]
When using block cipher modes of operation, it is crucial to consider the security implications, including the choice of IV, the block size, and the potential for vulnerabilities like padding oracle attacks in some modes. Proper implementation and choice of mode can significantly enhance the security of a cryptographic system.
Block cipher mode of operation gallery[edit]
-
Block Cipher Modes of Operation
-
GCM Galois Counter Mode with IV
-
ECB Encryption
-
ECB Decryption
-
Tux
-
Tux Encrypted ECB
-
Tux Encrypted CTR
-
CBC Encryption
-
CBC Decryption
-
CBC Example v3